Authored by Nadine Touzeau*,
Abstract
When we study the emotions of the victims of certain cyber-attacks, a large majority of them display behaviors of discomfort and stress. These people feel personally involved in the impact of the cyber-attack. Many feelings, impressions and emotions trigger attitudes, behaviors that move from guilt to seeking comfort, help, support, etc. Depending on the cyber-attack, many more or less common emotions seem to be emerging. But also new attitudes in order to seek answers, comfort or justification for an act, word, comment, position, criticism or even insults issued or received. We can rely on the scientific theories I have developed concerning my research on Behavioral Differentiations between the Real and the Virtual Space, which are the subject of several scientific publications [1-14] in order to understand some of these new behaviors.
“Avatarization”, “Transversal Zone” and “Virtual Intelligence” are revealed all the more in the face of these new behaviors that the virtual puts forward... My theories, which can also be found in my books on Net-profiling [15], highlight other behaviors that social networks are increasingly highlighting. Humans adapt and or modify themselves by or through the virtual.
Keywords:Net profiling; Transverse zone; cyberspace; virtual space; Behavioral differentiation; Avatarization; Virtual Intelligence; Violation of private life
Introduction
“I felt like it was my fault, that I had done something to deserve this,” says Kelly, a victim of cyberbullying on Facebook [16]. She added: “I often thought of ending my life at that time. I’ve sometimes tried. I mean, by scarifying my skin, that kind of thing.” Kelly was closing in on herself without understanding the content of the harassment she was subjected to by someone she doesn’t even know, after putting a “Like” in a picture. Kelly, withdrawn and now epileptic, will be physically beaten by her detractors at school.
In the same newspaper, Lucie shares her feelings about the aftermath of experiencing a situation similar to Kelly’s: “You don’t realize, at first, that you’re being harassed. Insults destroy selfconfidence, because they never stop. It’s from sunrise to sunset, and it puts psychological pressure on you. I was sure I did something wrong, but today, with hindsight, I know very well that I didn’t.”
During one of my own missions concerning a cyberbullying victim, this 37-year-old adult felt able to handle this attack on her own and quickly lost her footing by isolating herself. Beyond that, this person felt stupid not to have seen this cyber harassment coming because she is an adult. She felt helpless and raped inside herself because of the violent words she experienced on the Internet. “Those words were wrong, I couldn’t defend myself against all those people I don’t know who also cyber-harassed me. They talked about me as if they knew me, they judged me when in fact everything was wrong. But no one was listening to me.” She added: “And neither could justice help me!”.
Testimonies that highlight feelings, emotions and experiences of attacks on the victims’ personal lives, but also on their intimacy, which is their own and personal. A form of internal intrusion that they themselves could not have suspected possible to achieve. An emotional abuse that some victims have compared to rape. We will develop these feelings, emotions based on testimonies and facts and based on my own scientific theories.
Discussion
“The growth and prevalence of the use of New Communication Technologies in our societies has generated new behaviors and new forms of relationships between individuals,” says Catherine Blaya [17]. These new behaviors at the heart of my research work on Behavioral Differentiations between the Real and the Virtual Space are becoming more and more apparent.
Avatarization
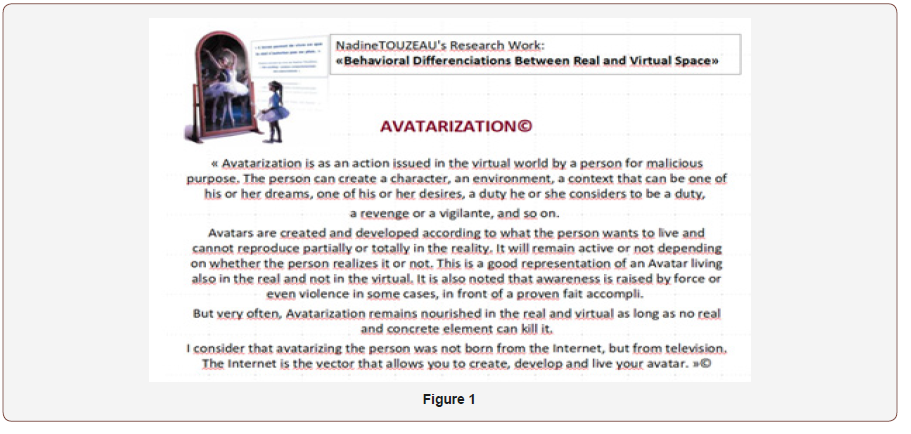
Avatarization, one of my theories, highlights [18] some behavioral aspects studied on cybercriminals ranging from cyberbullyers to black hat. What emerges in common on these cyber delinquents is the fact that behind the screen they feel free. Free to live what they want. Free to express themselves beyond their own thoughts. Free to let go completely until they surpass themselves. Free to exceed performances according to their own desires even if they are devoid of reality and meaning. Totally free in every way.
This freedom they discover is measured on the results of what they get. Strengthened by being considered credible in their act and behavior, they often multiply this freedom of expression, experience and feeling. Depending on the profile of the cybercriminal, they may develop even more behaviors that are totally out of line with their own profile. That creates one or more characters that they live behind the screen and animates according to the exchanges. Avatars that sometimes they reproduce everything or part of everything in the real world. This allows them to evacuate, to discover a form of power over others, to let go where they would remain silent in reality, to live what they are not, to be someone else while remaining more or less themselves.
The case of Kelly or Lucie highlights that cyber-bullyers use the connected tool to incriminate, defame and harass these young girls. Behind the screen, it is easier to hide, to let go in excess using words than in real life most of the time cybercriminals would not say. Insults about the physical are written on social networks punctuated by violent words that often criticize the person by characterizing them differently than what they are. Strangers feed these harassments on the web without knowing the victim or even being able to defend themselves. Internet users will only rarely take this into account and as the damage is done, that is all we will remember.
There is a feeling of intrusion into the victim’s life, even if the comments are false because the doubt settles in: “I deserved it” thinks many of them. Their personal life is dissected on the web and everything goes through it, with false interpretations, value judgments. It’s hurtful, demeaning. The victim is powerless in the face of her life peeled on the web. Often without even knowing the person, one finds oneself defamed without any apparent reason. Above all, there is no reflection, no questioning, just a judgment. We judge on a written document without checking. We judge on an image without worrying about anything. Criticism is easy. Then, others believe without even questioning themselves and follow the initiator of criticism without thinking.
They all conceal the fact that a human being will receive this stream of criticism. Avatarizing their image behind the screen and letting go more easily than if they were facing the person, allows them to be more virulent. They spill words without understanding their significance, without imagining the harm it does. They evacuate their own ills. We have seen cases where, once the cyber bullyer was arrested after his victim committed suicide, the cybercriminal said that he did not understand why his victim committed suicide and added that “it was only a game”.
These cyber-offenders allow themselves to play roles that they could not play in the real world. Thinking they are rusticated, knight or Dark Vador, no matter what role they want to play, sometimes even several roles, the Internet helps them to live these roles. Personalities who create or multiply themselves according to the virtual target, sometimes known in reality, in order to satisfy needs to express themselves in ways other than what reality can authorize. It happens that some profiles reproduce in reality what they experience in the virtual world. Video games for car racing or war have seen cases like this.
An Internet addiction by game or anything else, obviously does not help the results of behavioral changes behind the screen. They would tend, like any addiction, to amplify them. Behind the screen some profiles allow themselves everything. And character traits from his profiles are more visible. A person has a critical, negative tendency, will tend to be even more critical behind the screen. If the Internet emphasizes narcissism, it does the same for people with a destructive tendency (Figure 1).
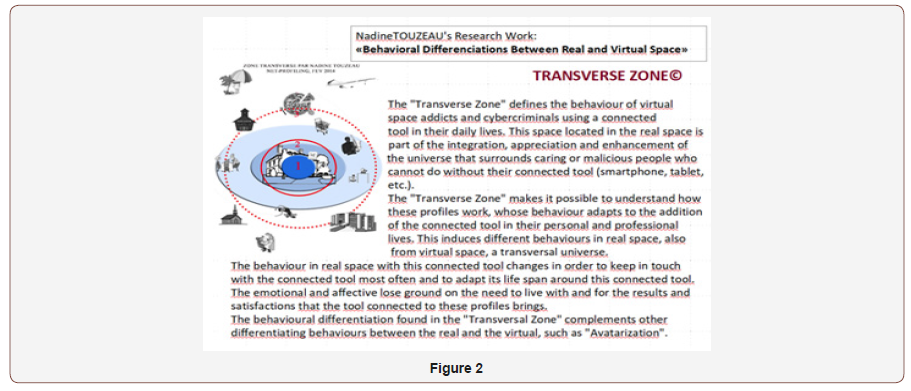
These cybercriminals live in the real connected to this virtual. In my theory of “Zone Transverse” [20], it is argued that the way of living with this connected tool is also changed. Wherever you are, the connected tool will be more important than any other material such as a great friend or professional partner, which means that if this tool is damaged, disconnected or lost, an emotional imbalance sets in, creating emotions that only a human being can cause. The connected tool has a place in the lives of cybercriminals, especially since it is the link that allows them to commit their crime. It changes the way we work, live every day, be with family or as a couple. It becomes an almost vital center of interest that will reduce human relations (Figure 2).
Virtual intelligence
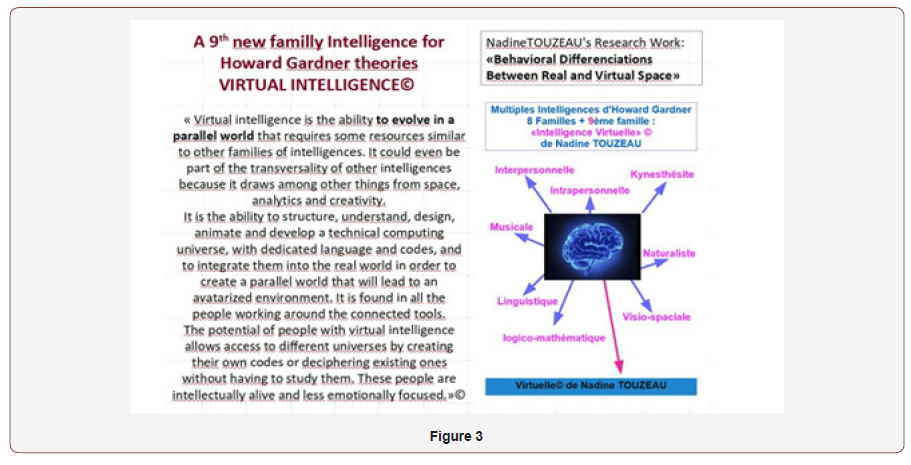
The previous theories, “Avatazisation” and “Zone Transverse” highlight, among other things, that these cybercriminals have developed new intelligence that is the subject of one of my theories [21]. Intelligences adapted to cyberspace in order to live better in it even if the human being lives in reality. A form of life in two worlds at the same time that forces us to mix the two worlds in our daily lives.
These developments of new intelligences adapted to the virtual world are changing our habits, our way of living, thinking and behaving. Sometimes reproduced in reality, these human mutations have not yet revealed their secret and will surprise us in the years to come. The cybercriminal changes his emotions and feels behind the screen, not necessarily the victim as the next chapter of the discussion shows.
Playing a role behind the screen, or even several, living them, knowing how to live behind the screen, knowing the codes, the laws erected, moving easily, also lasting as long as the notion of time is debatable in virtual space [17] is not required for any profile. The real world versus the virtual world is more different than it seems. Humans live in both worlds by being palpable, by living more emotions and feelings, by having all their senses activated, etc., in reality. Physically, man is in the real and can live in the virtual in certain moments in the form he wants. New intelligences that deserve to be worked on. Especially since they will explain differences, here again, between what reality allows us to live, such as the senses [20] (Figure 3).
Analysis emotions
An analysis of the feelings of cyber-attack Companies highlights the following: “The companies affected by these cyber-fraud and cyber-attacks, in addition to the direct financial loss in dollars associated with fraud by the cyber-criminal, have literally suffered a shock. A shock comparable to that felt during the first burglary, the shock of a crisis of confidence during a embezzlement or the shock of a totally unexpected executive reshuffle. [24]. An intrusion into the Campanies’ professional intimacy considering that most of the time the business is part of their life, especially since they spend most of their time at work. A violation of their data. Purely confidential information is in the hands of strangers who can arrange it as they wish and disclose it to anyone. A real violation of its know-how that escapes everyone because the data goes on the Internet, with no limit of distribution or borders. After a surprise effect, the emotion of robbery is indeed very strong among the victims, but not as a physical robbery due to the uncontrolled spread of data. A fear is developing that others will know and use his professional approach, his know-how, his customers, his research and development, his bank accounts, the data of a company life. The question is also how did you get robbed in this way? What have we omitted in our security? Sometimes, we are asked why.
We notice an outpouring on the internet of emotion, felt, experienced very personally. Personal comments, intimate photos, shared experiences, opinions that are revealed in small groups fill the posts on social networks. Everyone can read them, even if the parameters indicate otherwise. A copy and paste, a screenshot and everything is shared. Without obscuring the technical cyberattacks. These elements play into the hands of malicious people, whether they are cyber-bulliers, emotional scammers, or trap you with software or technical tools. In fact, when the victim discovers this, astonishment is one of the first emotions expressed. Why me? Why me? Why did they react like that against me? What did I do? Or what shouldn’t I have done?
Contrary to the entrepreneur, the intrusion is not immediately put forward in the face of this cyber-crime, but rather a revealed intimacy that highlights a dis-comfort. The inconvenience of everyone reading something unpleasant. The gene that we see in personal elements diffused on the web. The inconvenience of being exposed a little bit on the Internet when you didn’t want to reveal something or when you are talked about in a certain way. Then a more or less accepted loss of control is established. The one it’s too late, it’s divulgated and there’s nothing we can do anymore. The one that a part of us has been touched with words, images, behaviors that have destabilized the victims of what is happening and without being able to stop or even manage it.
What is revealed when cybercriminals are questioned after a crime committed after their care is that they do not see the harm done. For them, the human has not been reached. This implies that to the extent that they have not seen their victim in the real world (even if they sometimes know him/her), they do not seem accessible and therefore may suffer from what they receive from them. Some cybercriminals even mention that it was a game. However, this game can kill individuals by collateral damage if the victim commits suicide as a result of the cyber-crimes received. Not seeing their victim means that some cybercriminals do not really feel responsible for how their victim feels. They do not feel even less like an executioner. The weight of their act on their victim is much less important than what the victim feels. A greater gap than an act committed in reality.
Being insulted in the street does not have an intrusive effect on one’s private life to the extent of being insulted in a social network. Moreover, people commit suicide more as victims of cyberbullying, sex tape, emotional scams or ransomware, scams the President than being robbed of their house, stolen documents from their companies, stolen research work or insulted in the street. The stress generated on the web comes from the feedback from the reaction of the act we have undergone. Insults towards a person, often for no reason, multiply and are fed by profiles who like to take a stand without knowing why, without even knowing the person or having a psychiatrically disturbed profile.
What will people think of me? Who can read this? What will people remember about me? Why say such bad things? Why steal a lifetime’s work? Who’s going to believe me when I defend myself. Because he’s going to family to defend himself. We will have to fight to overcome such often-underestimated challenges when they occur. We think it’ll pass. It’s not palpable so it’s not an insult on my Facebook wall, a sex tape video on YouTube among others, a confidential document that’s stolen but stays behind the screen. Time will teach the victim that this is not the case. That these cyber-crimes are much more serious with much more impact than previously thought. More than an insult on the street, a computer theft, a burglary.
You can’t delete everything on the web. The writings as well as the moods of people who want to hurt you. And these writings remain for life. Everyone has access to it worldwide, with no limit on reading. Anyone can believe that or not. But it is read and known, viewed or watched. By people who would not normally have had access to anything from you without the intermediary of these cybercriminals who have disclosed confidential information about their victims for X and Y reasons. Barely exposed on the Internet, all or part of their privacy, victims have to first become aware of what is happening and then manage an unexpected situation that they do not understand.
Emotions arise and harm victims who feel betrayed, publicly soiled. If errors have been written about these victims, the feeling of talking about them as a stranger, of not understanding what is said about them because it does not correspond to them is very important. A discrepancy between their person whom their loved one knows and what is written on the Internet. Thus, some victims say that their name and image is them, but not the text that goes with it. They never said or thought that. Some cases have mentioned that they could not even defend themselves. That they could do nothing but suffer from photos or videos published without their knowledge, defamatory words or harassers written without their knowledge. Whatever these victims do or say, they cannot defend themselves or stop this situation. Sometimes defending oneself means putting fuel on the fire and feeding even more hate speech.
A deceleration between who we are and who we describe on the Internet is created to destabilize the victim rarely with defence resources. But this shift is likely to be received as real by the victim. They consider that they have earned what is happening and that there is necessarily truth in the statements written on the Internet. These cyber-crimes, which do not use only limited software or techniques, or are almost exclusively committed by man, are sometimes deliberate in an attempt to destroy a person. Avengers, jealous, who convince and lead others to try to kill their personal target. Salaried employees who take revenge for something they didn’t like or simply infiltrate the company to spy and steal data. These acts are intrusive acts, which affect the person, the victim. Without warning or sometimes being informed because the rumour and defamation triggered by malicious people rarely reaches the victim’s ears quickly. Cyber offenders like to collect very personal information. The more they have, the more their attacks will hurt. So, these cyber- offenders must approach their victims at least on the web. More than an intrusion into their private lives, some victims seem to give reason to the flood of criticism and insults they are subjected to in order to lose their own identity.
Conclusion
From an innocuous situation, a simple “Like” on an image on a social network, a revealed opinion without any offbeat, a diverted photo, a stolen video and your life can become a hell without your tormentors being worried.
The feelings and emotions are increased ten- fold on the cyber-delicious victim than victims of malicious acts in the real world. A destabilization takes place losing much of reality. Both the cybercriminal who seems not to realize that a human being is attacked by him, the victim who forgets who she is in the face of cyberattacks. A technostress develops in the victim in a disproportionate way in front of the intrusive behavior that makes the cybercriminal. Intrusion considered more important in the feeling and the emotion in the virtual than the real one be- cause of the space of diffusion and the lack of defense that the virtual causes.
Add to this the legal vacuum in order to defend oneself and to remove as quickly as possible the abuses that the victim did not necessarily create. In fact, a feeling that the cyber- criminal has been right to harm the victim since everything gives him reason develops, without anyone wanting to talk or fight. Ac- quire or even submit to these cyber criminals who can, with complete impunity, divulge your lives in whatever form they want without being worried. Faced with this finding, how can the victim express himself, feel a real victim and be sup- ported, what are wrong is considered at the height of what it is? The intrusion of victims’ privacy may also be this: underestimating the potential of cyberoffending by not considering them as high as they are.
To read more about this article...Open access Journal of Biology & Life Sciences
Please follow the URL to access more information about this article
To know more about our Journals...Iris Publishers





No comments:
Post a Comment